如何在 Ubuntu 16.04 上为 Nginx 生成和配置自签名 TSL/SSL 证书
在本文中,我们将学习如何在 Ubuntu 16.04 上为 Nginx 生成和配置自签名 SSL/TSL 证书。TSL 是传输层安全协议,其前身是 SSL(安全套接字层),用于保护普通流量在加密数据包中传输,流量从服务器传输到客户端,并且不会被外部入侵者拦截。证书还可以帮助用户验证他们访问的网站身份是否正确。
如果我们没有与站点或服务器实例关联的任何正确的域名,则可以使用自签名证书。
先决条件
为了完成此演示,我们需要以下要求。
- 具有 sudo 权限的非 root 用户。
- 已安装 Nginx Web 服务器。
在服务器上安装 OpenSSL 包
我们需要在服务器上安装 OpenSSL 包,以下是 Ubuntu 16.04 上安装 SSL 的命令
$ sudo apt-get install openssl Output: Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: libyaml-0-2 python-crypto python-ecdsa python-jinja2 python-markupsafe python-paramiko python-pkg-resources python-setuptools python-six python-yaml sshpass Use 'sudo apt autoremove' to remove them. Suggested packages: ca-certificates The following NEW packages will be installed: openssl 0 upgraded, 1 newly installed, 0 to remove and 13 not upgraded. Need to get 491 kB of archives. After this operation, 956 kB of additional disk space will be used. Get:1 http://in.archive.ubuntu.com/ubuntu xenial-updates/main amd64 openssl amd64 1.0.2g-1ubuntu4.1 [491 kB] Fetched 491 kB in 1s (283 kB/s) Selecting previously unselected package openssl. (Reading database ... 92688 files and directories currently installed.) Preparing to unpack .../openssl_1.0.2g-1ubuntu4.1_amd64.deb ... Unpacking openssl (1.0.2g-1ubuntu4.1) ... Processing triggers for man-db (2.7.5-1) ... Setting up openssl (1.0.2g-1ubuntu4.1) ..
创建自签名 SSL 证书
SSL 将使用公钥和私钥的组合工作,其中 SSL 密钥将位于服务器上以加密发送到访问服务器的客户端的数据。SSL 将与请求内容的公众或客户端共享,并将用于解密与 SSL 密钥关联的数据。
以下是使用 OpenSSL 创建自签名证书和密钥对的命令。
$sudo openssl req -x509 -nodes -days 365 -newkeyrsa:2048 -keyout /etc/ssl/private/nginx-demosite.key -out /etc/ssl/certs/nginx-demosite.crt
Output: Generating a 2048 bit RSA private key ................... ................... ..........+++ ..... ...+++ writing new private key to '/etc/ssl/private/nginx-demosite.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:IN State or Province Name (full name) [Some-State]:TELENGANA Locality Name (eg, city) []:HYDERABAD Organization Name (eg, company) [Internet Widgits Pty Ltd]:demosite.com Organizational Unit Name (eg, section) []:demo Common Name (e.g. server FQDN or YOUR name) []: demosite Email Address []:admin@demosite.com
由于上述命令将生成带有证书的两个密钥文件,因此它会询问一些与我们即将生成的证书相关的信息。
以下是我们在上述命令中使用的选项的说明 -
openssl - > This is a command line tool to create the certificates and keys. -req - > X.509 is a public key infrastructure standard for the SSL the ‘req’ is the sub command which allows to specify the standards for the SSL, the –x509 specifies that we want to generate self-signed certificate instead of generating the certificate signed. -nodes - > As we want to read the Nginx to read the certificate file with our any password or user interventions, if we don’t use this command the it will ask for a passphrase. -days 35 -> This will set the validity of the certificate for one year. -newkey rsa:2048 - > This option specifies that we will generate a new certificate and key with 2048 bit encryption. -keyout -> This will tell the OpenSSL to place private key which is generated. -out -> This will tell the OpenSSL to place the certificate file which is generated.
生成 SSL 密钥后,我们将使用 Diffie-Hellman 组强化 SSL 证书。
以下是强化 SSL 证书的命令。
$sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 2048 Output: Generating DH parameters, 2048 bit long safe prime, generator 2 This is going to take a long time .................................................+.+...............+....................................................... ........................+.......................................................................+.......................... ......................+......................................... .......................................................... ........................................................................................................................... .....................................................+..............+.......+..........+.................................+. ..................................................................................+.................................+.....+ ......................+...............................+...................................................................................................................................................+............................................................................................................+.......................................................................................................+.....................+............................................................... ….
使用自签名 SSL 证书配置 Nginx
由于所有证书和密钥都已生成并保存在 /etc/ssl 目录中,因此我们需要修改 Nginx 配置文件以使用这些生成的文件。
我们需要更改一些配置,我们需要在配置文件中调整这些配置。
包含 SSL 证书和密钥文件的代码段
$ sudo vi /etc/nginx/snippets/selfsigned.conf
输出:ssl_certificate /etc/ssl/certs/nginx-demosite.crt; ssl_certificate_key /etc/ssl/private/nginx-demosite.key;
代码段包含强大的 SSL 设置,可以在以后的配置中与任何证书全局使用。
$ sudo vi /etc/nginx/snippets/ssl-params.conf Output: ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers "EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH"; ssl_ecdh_curve secp384r1; ssl_session_cache shared:SSL:10m; ssl_session_tickets off; ssl_stapling on; ssl_stapling_verify on; resolver 8.8.8.8 8.8.4.4 valid=300s; resolver_timeout 5s; # Disable preloading HSTS for now. You can use the commented out header line that includes # the "preload" directive if you understand the implications. #add_header Strict-Transport-Security "max-age=63072000; includeSubdomains; preload"; add_header Strict-Transport-Security "max-age=63072000; includeSubdomains"; add_header X-Frame-Options DENY; add_header X-Content-Type-Options nosniff; ssl_dhparam /etc/ssl/certs/dhparam.pem;
调整 Nginx 服务器块以处理 SSL 请求。
由于所有代码段都已准备就绪,我们现在将在 Nginx 配置文件中启用 SSL。
$ sudo vi /etc/nginx/sites-available/default-ssl
Output:
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
server_name IP addrres or demositename;
include snippets/self-signed.conf;
include snippets/ssl-params.conf;
location / {
# First attempt to serve request as file, then
# as directory, then fall back to displaying a 404.
try_files $uri $uri/ =404;
}
}在服务器上应用 Nginx 更改
由于我们已更改 Nginx 的配置并添加了代码段,因此我们将测试 nginx 配置文件。
以下是检查 Nginx 语法错误的命令。
$ sudo nginx –t Output: nginx: [warn] "ssl_stapling" ignored, issuer certificate not found nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
所有 Nginx 配置似乎都正确,我们现在将重新启动 Nginx,以便配置将应用于服务器。
$ sudo systemclt restart nginx.
配置防火墙以允许 SSL
以下是检查防火墙状态的命令
$ sudo ufw status Output: Status: active To Action From -- ------ ---- Nginx HTTP ALLOW Anywhere OpenSSH ALLOW Anywhere Nginx HTTP (v6) ALLOW Anywhere (v6) OpenSSH (v6) ALLOW Anywhere (v6)
首先,我们将列出防火墙提供的所有配置文件。以下是列出应用程序配置文件的命令列表。
$ sudo ufw app list Output: Available applications: Nginx Full Nginx HTTP Nginx HTTPS OpenSSH
由于“Nginx Full”配置文件未被允许,我们将允许“Nginx Full”并从防火墙中删除“Nginx HTTP”,然后我们将检查允许“Nginx Full”配置文件后的防火墙状态。
$ sudo ufw allow 'Nginx Full' Rule added Rule added (v6) $ sudo ufw delete allow 'Nginx HTTP' Rule deleted Rule deleted (v6) $ sudo ufw status Output: Status: active To Action From -- ------ ---- OpenSSH ALLOW Anywhere Nginx Full ALLOW Anywhere OpenSSH (v6) ALLOW Anywhere (v6) Nginx Full (v6) ALLOW Anywhere (v6)
使用加密测试 Nginx 配置
打开任何浏览器,并尝试使用系统的 IP 地址通过 https://IP-Address 访问服务器。
https://ip-address-or-dns-name
访问站点后,我们将看到一条警告消息,指出证书无效,因为它是自签名的。
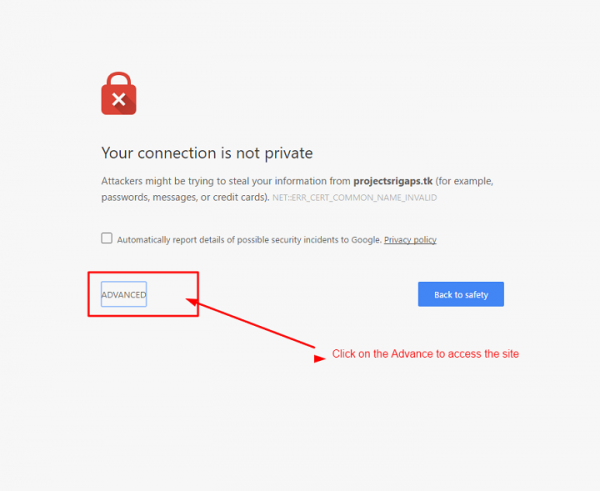
由于 SSL 未进行数字签名,我们需要单击“高级”以继续。
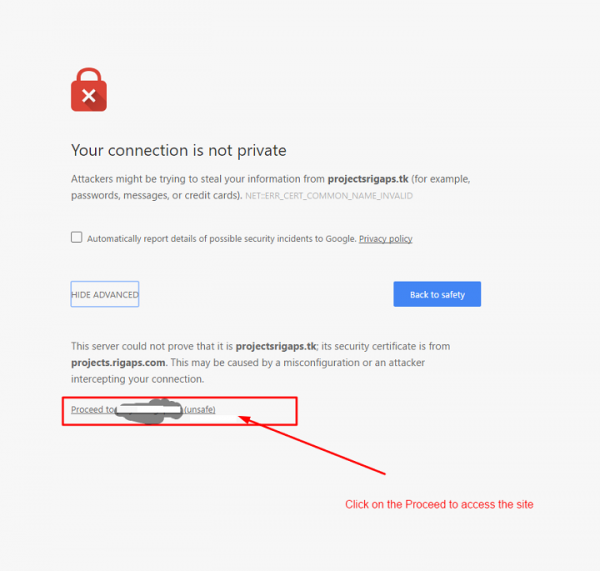
单击“继续访问(不安全)”以访问站点。
通过此设置,我们可以创建自己的自签名 SSL/TSL 证书,并配置 Nginx 使用 SSL 配置,我们还可以使用强加密让客户端安全地连接和提供请求,这将防止入侵者访问数据。


 数据结构
数据结构 网络
网络 关系型数据库管理系统
关系型数据库管理系统 操作系统
操作系统 Java
Java iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C 编程
C 编程 C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP