- Metasploit Tutorial
- Metasploit - Home
- Metasploit - Introduction
- Metasploit - Environment Setup
- Metasploit - Basic Commands
- Metasploit - Armitage GUI
- Metasploit - Pro Console
- Metasploit - Vulnerable Target
- Metasploit - Discovery Scans
- Metasploit - Task Chains
- Metasploit - Import Data
- Metasploit - Vulnerability Scan
- Metasploit - Vulnerability Validation
- Metasploit - Exploit
- Metasploit - Payload
- Metasploit - Credential
- Metasploit - Brute-Force Attacks
- Metasploit - Pivoting
- Metasploit - Maintaining Access
- Metasploit - MetaModules
- Metasploit - Social Engineering
- Metasploit - Export Data
- Metasploit - Reports
- Metasploit Useful Resources
- Metasploit - Quick Guide
- Metasploit - Useful Resources
- Metasploit - Discussion
Metasploit - Vulnerable Target
A vulnerable target is a machine or device with an unpatched security hole. It makes the host vulnerable, which is the target in this case.
For testing purpose, Rapid7 has created a VM machine with plenty of vulnerabilities. Keep in mind that you are not allowed to penetrate any device without permission. Hence, you need to download metasploitable which is a Linux machine.
Metasploitable can be downloaded from − www.information.rapid7.com/
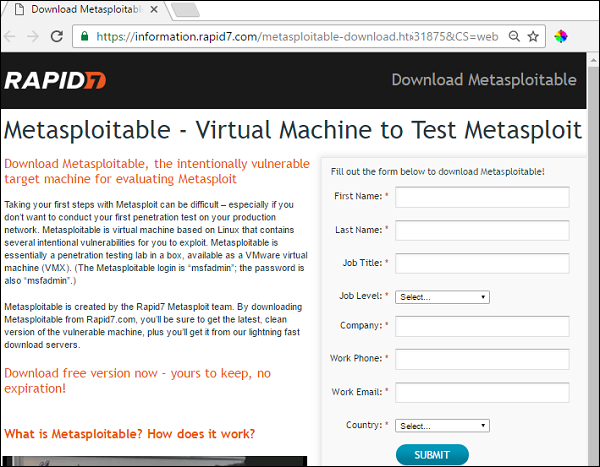
Fill out the form to register yourself. Next, you will get the following screen with a direct link to download Metasploitable.
Next, open the VirtualBox Manager and go to Machine → New.
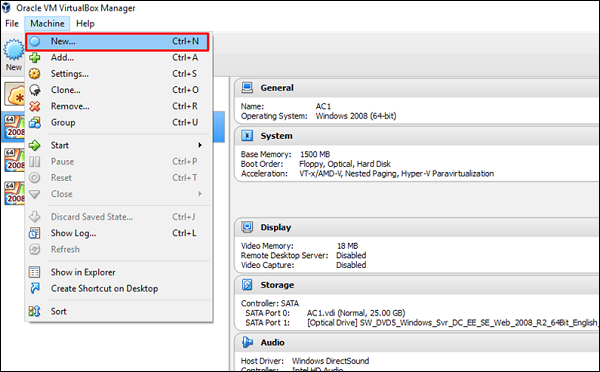
Click “Use an existing virtual hard disk file" and browse to the location where you have downloaded Metasploitable. Click Open.
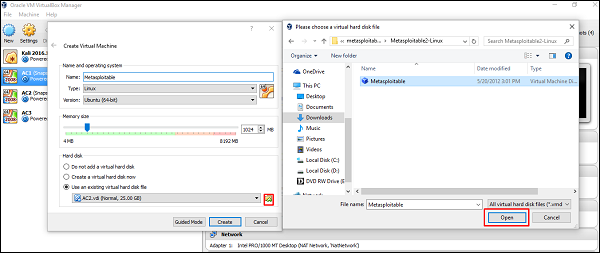
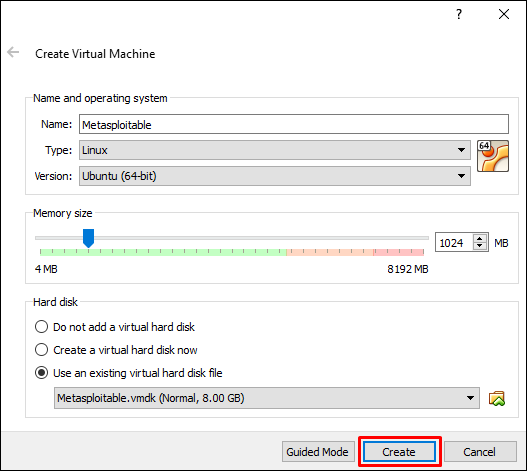
On the next screen, click Create.
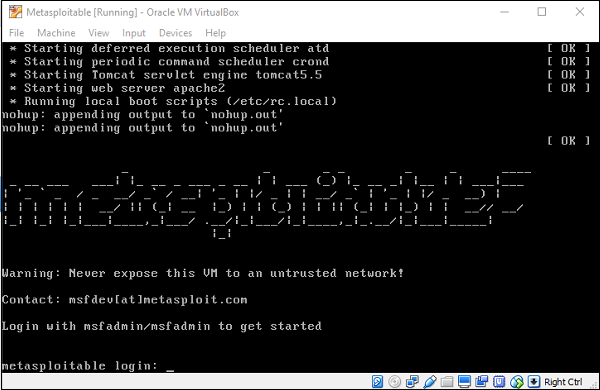
Now, you can login to Metasploitable using the default username: msfadmin and password: msfadmin.