
- Unix Commands Reference
- Unix Commands - Home
autrace Command in Linux
The autrace command is a valuable tool for system administrators and security professionals who need to audit system calls made by a process. It functions similarly to strace, but with a focus on generating audit logs that can be reviewed later.
autrace is a part of the Linux Audit system, which is designed to track security-relevant information on your system. When you execute autrace, it adds audit rules to trace a process, then runs the specified program with any arguments passed to it. The audit logs generated can be found in the audit daemon if it's running, or in syslog.
Table of Contents
Here is a comprehensive guide to the options available with the autrace command −
- Install autrace Command in Linux
- How to use autrace Command in Linux?
- Examples of autrace Command in Linux
- Alternatives of autrace Command in Linux
Install autrace Command in Linux
Understanding and utilizing the autrace command can significantly enhance the security and auditing capabilities of a Linux system. Let install autrace on Linux −
For, RedHat/CentOS-based Systems
The autrace command in Linux is a powerful utility that is used to trace the system calls made by a program and the signals received by the program. Let’s check for installation −
which autrace
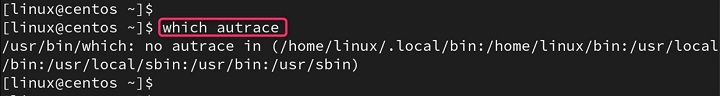
Install autrace
It can be installed using the audit package but is specifically designed for use with the Linux Audit System −
sudo yum install audit
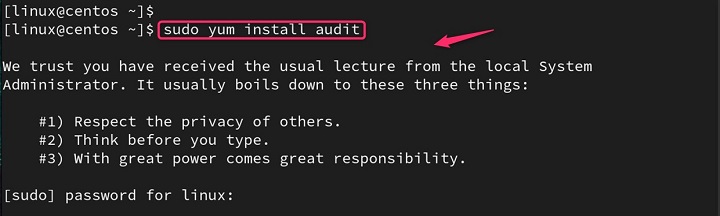
Similar to Ubuntu/Debian, audit provides autrace and its dependencies.
How to use autrace Command in Linux?
The autrace command adds audit rules to track the activities of a process, which can be invaluable for system administrators and security professionals who need to analyze the behavior of applications in a Linux environment.
Syntax
To use autrace, simply follow the syntax −
autrace [program] [options] [program-args]
The options are available with the autrace command. Here's a breakdown of the different options available with the autrace command in Linux −
| Options | Description |
|---|---|
| -h | Displays helpful information about autrace. |
| -V | Shows the version of autrace. |
| -n | This option allows the traced program to be run in a new namespace. |
| -r | This option limits the system calls collected to those needed for analyzing resource usage. This can be particularly useful for threat modeling as it helps to save space in logs by focusing only on the most relevant data. |
| -s <syscall_list> | Limits tracing to specific system calls. Provide a comma-separated list of system calls you want to track (find the list in /usr/include/asm/unistd.h). |
| -a <audit_flags> pen_spark | Sets additional audit flags for the generated audit records. Refer to the auditctl man page for details on available flags. |
| -c <buffer_size>: pen_spark | Sets the size of the audit message buffer. |
| man autrace | Explore the man page (man autrace) for a comprehensive explanation of all options and their functionalities. |
| auditctl | Explore the auditctl man page to understand additional audit flags usable with the -a option of autrace. |
Important Note − These options should be used with caution as they can significantly impact the amount of data logged and system performance.
Example of autrace Command in Linux
autrace is a valuable tool for auditing processes in Linux. Here are some examples of how to use autrace with various options −
Example 1: Basic Usage
To trace the system calls made by the ls command and then search the audit logs for entries related to this command, you could use −
sudo autrace /bin/ls ausearch --start recent -p [PID] -i
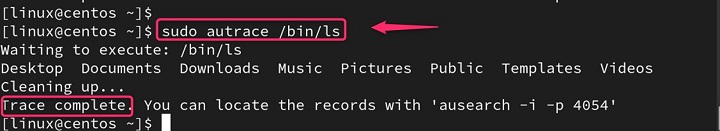
In the above command, [PID] should be replaced with the process ID of the ls command.
For instance, to trace the execution of the ls -l command, you'd use −
sudo autrace ls -l
Note − Before running autrace, it's crucial to clear any existing audit rules using −
sudo auditctl -D

This ensures autrace creates its own clean set of rules for accurate tracing.
Example 2: Resource Usage Mode
For resource usage mode, which uses the -r option, the commands would be −
sudo autrace -r /bin/ls sudo ausearch --start recent -p [PID] --raw | aureport --file --summary sudo ausearch --start recent -p [PID] --raw | aureport --host --summary
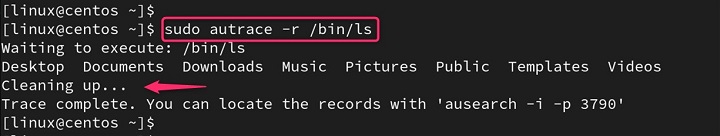
Users can also replace [PID] with the traced process ID.
Example 3: Repeating autrace
If you want to run autrace repeatedly, you can achieve this using a loop or script. For example −
while true; do autrace <program> ; sleep 5; done
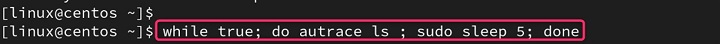
This will continuously run autrace on the specified program every 5 seconds.
Example 4: Specifying a Trace Duration
autrace doesn't have a built-in option to limit the tracing duration. However, you can achieve a similar effect by combining it with tools like timeout. Here's an example tracing a program for 10 seconds −
timeout 10s autrace <program>
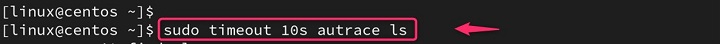
This will run autrace on the program for a maximum of 10 seconds and then terminate it.
Example 5: Limiting Traced System Calls
autrace can trace all system calls by default. To limit this, use the -s option with a comma-separated list of system calls to trace. You can find a list of system calls in the /usr/include/asm/unistd.h header file.
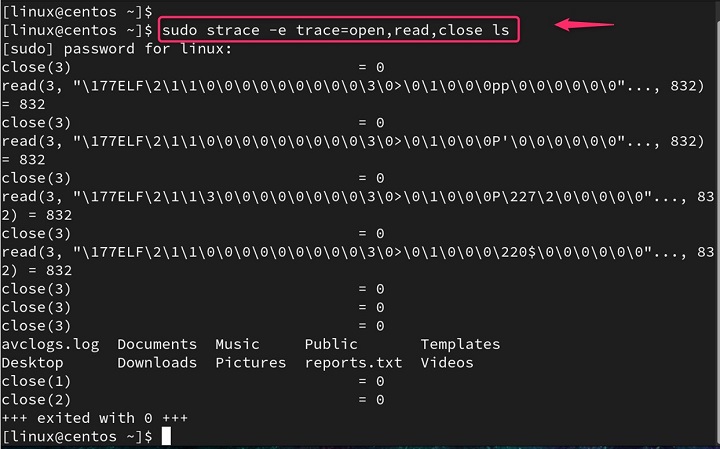
For example, to only trace the open and read ls program −
sudo strace -e trace=open,read,close ls
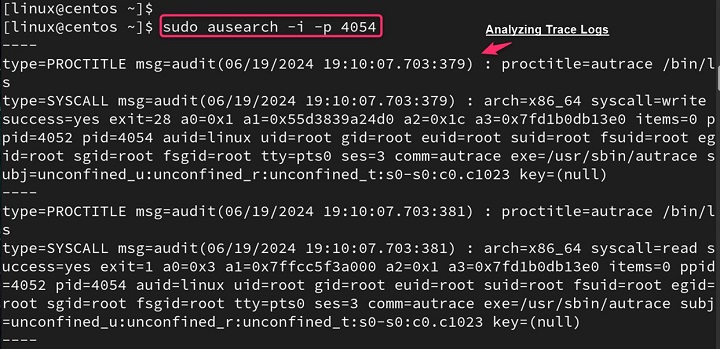
Analyzing Trace Logs with ausearch
The ausearch commands are part of the Linux Audit System and are used to search from the audit logs.
This command helps search the audit logs. The -i option interprets numeric values into human-readable text, and -p <pid> allows searching for a specific process ID (PID) −
sudo ausearch -i -p <pid>
Analyzing Trace Logs with aureport
Once you have filtered results with ausearch, use aureport to generate a report. The --raw option provides raw input to aureport, and additional flags like -f and -i enable reporting on specific details like files and interpretations.
aureport --raw -f -i < ausearch output > report.txt
Manual Page
The autrace command is a part of the audit package, and more information about its usage can be found on the man pages.
man autrace
Alternatives of autrace Command in Linux
autrace is a powerful command that provides insights into the system calls made by processes, aiding in security and resource usage analysis.
| Feature | strace | ltrace |
|---|---|---|
| Focus | System calls | Library calls |
| Information provided | Detailed interaction with the kernel | Function calls within libraries |
| Useful for | Debugging system calls, identifying resource usage, analyzing process flow | Debugging library usage, analyzing performance issues. |
| Common Options | ||
| -p<pid> | Trace a specific process | Trace a specific process |
| -e <syscall> | Trace only specific system calls | Trace only specific library calls |
| -o <file> | Redirect output to a file | Redirect output to a file |
| -v | Verbose mode, providing more details | Verbose mode, providing more details |
| -f | Follow forks (trace child processes) | N/A |
| -t | Print timestamps for each system call | N/A |
| -L <library> | N/A | Trace calls only to a specific library |
| -g | N/A | Display function arguments on the stack |
Note − autrace command allows administrators to gain detailed insights into how applications interact with the system, which can be crucial for troubleshooting, performance tuning, and security auditing.
Conclusion
The autrace command in Linux is a powerful utility that is used to trace the system calls made by a program and the signals received by the program. It is similar to the strace command but is specifically designed for use with the Linux Audit System.
The autrace command adds audit rules to track the activities of a process, which can be invaluable for system administrators and security professionals who need to analyze the behavior of applications in a Linux environment.
By following this tutorial, users can effectively utilize autrace to monitor and audit system calls on their Linux systems.