
- Unix Commands Reference
- Unix Commands - Home
ec Command in Linux
The ec command in Linux is a versatile tool used for processing EC (Elliptic Curve) keys within the OpenSSL library. It allows users to perform a variety of operations on EC keys, such as generating, checking, converting, and managing them.
Table of Contents
Here's a comprehensive guide to understanding the options available with the ec command.
Understanding ec Command
The ec command in Linux is a versatile tool used for processing EC (Elliptic Curve) keys within the OpenSSL library. It's a powerful command that allows users to generate, transform, and manage EC keys for various cryptographic purposes.
When using the ec command, it's crucial to handle private keys securely, especially when specifying passphrases and encryption methods. Always ensure that private keys are stored and transmitted securely to prevent unauthorized access.
How to Use ec Command in Linux?
The ec command is part of the OpenSSL toolkit, which is widely used for secure communication and data encryption. Understanding these options allows users to effectively manage EC keys, which are essential for modern encryption standards like TLS/SSL.
EC keys are favored in many cryptographic systems due to their efficiency and security. They require smaller key sizes compared to RSA for equivalent security levels, making them faster and less computationally intensive.
Here explore options of ec command in Linux −
| Options | Description |
|---|---|
| Input and Output Formats | |
| -inform DER|PEM | Specifies the input format. DER is an ASN.1 encoded format, while PEM is the default format, which is base64 encoded. |
| -outform DER|PEM | Specifies the output format, with the same options as -inform. |
| File Operations | |
| -in filename | Defines the input filename to read a key from. |
| -out filename | Specifies the output filename to write a key to. |
| -passin arg | Indicates the input file password source. |
| -passout arg | Indicates the output file password source. |
| Key Encryption | |
| -des, -des3, -idea | These options encrypt the private key with DES, triple DES, or IDEA ciphers before outputting it. |
| Key Components and Parameters | |
| -text | Prints out the public, private key components, and parameters. |
| -noout | Prevents output of the encoded version of the key. |
| -modulus | Prints out the value of the public key component. |
| -pubin | Indicates that a public key is read from the input file. |
| -conv_form arg | Specifies how the points on the elliptic curve are converted into octet strings. |
| -pubout | Outputs a public key instead of a private key. |
| -param_enc arg | Specifies the encoding of the curve parameters. |
| -engine id | Specifies the engine to be used. |
For more detailed information and examples, you can refer to the official OpenSSL documentation or the man page for the ec command.
Examples of ec Command in Linux
Below are some examples of how the ec command can be utilized in different scenarios −
- Generating a New EC Key
- Converting EC Key Formats
- Printing EC Key Components
- Encrypting EC Private Keys
- Extracting the Public Key from an EC Private Key
- Changing the Passphrase of an Encrypted EC Key
- Removing the Passphrase from an Encrypted EC Key
Generating a New EC Key
To generate a new EC private key, you can use the following command −
openssl ecparam -genkey -name secp256k1 -out private.key
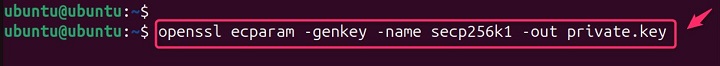
This command generates a new EC private key using the secp256k1 curve and saves it to a file named private.key.
Converting EC Key Formats
If you need to convert an EC key from PEM to DER format, the ec command facilitates this conversion −
openssl ec -in key.pem -outform DER -out keyout.der
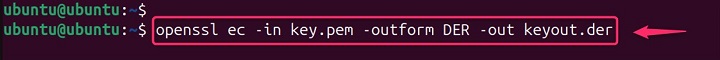
Here, key.pem is the input file in PEM format, and keyout.der is the output file in DER format.
Printing EC Key Components
To print the components of an EC key, including the private and public parts, use the -text option −
openssl ec -in key.pem -text -noout
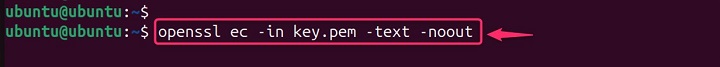
The -noout option ensures that only the text information is printed, without the encoded key.
Encrypting EC Private Keys
When you need to encrypt an EC private key using a cipher like triple DES, the command would be −
openssl ec -in key.pem -des3 -out keyout.pem
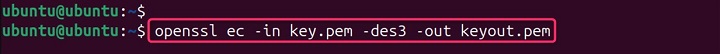
This command prompts for a passphrase to encrypt the key and outputs the encrypted key to keyout.pem.
Extracting the Public Key from an EC Private Key
To extract the public key component from an EC private key, you can use −
openssl ec -in private.key -pubout -out public.key
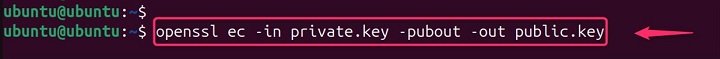
This saves the public key to a file named public.key.
Changing the Passphrase of an Encrypted EC Key
If you want to change the passphrase of an encrypted EC key, you can do so by reading the key with the old passphrase and writing it out with a new passphrase −
openssl ec -in key.pem -passin pass:oldpass -des3 -out keyout.pem -passout pass:newpass
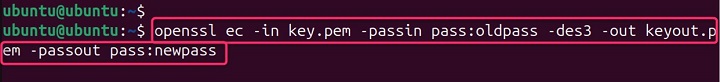
Replace oldpass and newpass with the old and new passphrases, respectively.
Removing the Passphrase from an Encrypted EC Key
To remove the passphrase from an encrypted EC key, simply read it in and write it out without specifying a cipher −
openssl ec -in key.pem -passin pass:oldpass -out keyout.pem
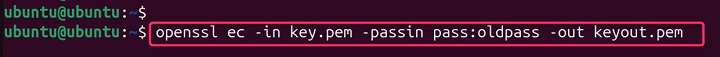
This prompts for the old passphrase and output a key without encryption.
These examples showcase the flexibility of the ec command in managing EC keys for secure communications. It's important to handle these operations with care, as they involve sensitive cryptographic material.
Conclusion
This guide aims to provide a clear understanding of the ec command and its options. Whether you're a system administrator, security specialist, or just a Linux enthusiast, mastering the ec command is a valuable addition to your skill set in the realm of Linux-based cryptography. Remember to always keep security best practices in mind when working with cryptographic tools and keys.
Always ensure that private keys are kept secure and that passphrases are strong and confidential. For more detailed information about the ec command and its options, you can refer to the OpenSSL documentation or the man pages.