
- Unix Commands Reference
- Unix Commands - Home
ciphers Command in Linux
OpenSSL is a widely used open-source toolkit that provides cryptographic functions and protocols like TLS/SSL for secure communication. The ciphers command is a utility included within OpenSSL specifically for managing ciphers suites, the cryptographic algorithms used for secure connections.
The ciphers command in Linux is specifically for the OpenSSL library and its tools. It deals with managing ciphers suites used for secure communication protocols like TLS/SSL. In a nutshell, it can list, manipulate, and analyze ciphers suites supported by OpenSSL.
Table of Contents
Here is a comprehensive guide to the options available with the ciphers command −
- Understanding ciphers Command
- Install ciphers Command
- How to Use ciphers Command in Linux?
- Examples of ciphers Command in Linux
- Alternatives of ciphers Command
Understanding ciphers Command
The ciphers command is a vital tool for anyone involved in system administration or cybersecurity. This command allows users to interact with OpenSSL to perform various operations related to Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols.
The ciphers command is used to display or modify the available ciphers algorithms for SSL/TLS connections. ciphers algorithms are essential for establishing secure communications over networks, and they work by creating encrypted connections using a series of handshakes and data transfers.
With the advent of TLS 1.3, there have been significant improvements in the efficiency and security of ciphers suites. TLS 1.3 has deprecated less secure key exchange mechanisms like RSA and introduced a more compact and robust set of ciphers suites. For example, TLS 1.3 recommends using suites like TLS_AES_256_GCM_SHA384 or TLS_CHACHA20_POLY1305_SHA256, which are designed to provide strong encryption with less computational overhead.
Install ciphers Command
The ciphers command isn't a separate program you can install in Linux. It's actually a built-in functionality of the OpenSSL library. So, if you want to use the ciphers command, you likely already have it.
Here's how to check, open your terminal and type −
openssl version
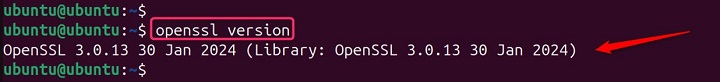
If OpenSSL is installed, this command will display the version information.
If OpenSSL is not installed, the installation process will vary depending on your Linux distribution. Here are some general steps −
Open your terminal. Use your distribution's package manager to install OpenSSL.
For Debian/Ubuntu-based systems −
sudo apt update sudo apt install openssl
For Red Hat/CentOS based systems −
sudo yum update sudo yum install openssl
Once OpenSSL is installed, you can use the ciphers command as explained earlier.
How to Use ciphers Command in Linux?
Here's a breakdown of the different options available with ciphers. The options available with ciphers are −
| Options | Descriptions |
|---|---|
| -h or --help | Displays a help message explaining all available options and usage. |
| -V or --version | Shows the version information of the ciphers command itself. |
| -s or --stats | Provides statistics on the available ciphers suites, including their strength and security level. |
| -v or --verbose | Increases the verbosity of the output, showing more details about the ciphers suites. |
| -ssl3, -tls1, -tls1_1, -tls1_2, -tls1_3 | Restricts the displayed suites to those compatible with specific TLS/SSL versions (e.g., -tls1_2 shows suites supported by TLS 1.2 only). |
| -psk | Includes ciphers suites that utilize Pre-Shared Key (PSK) authentication. |
| -srp | Includes ciphers suites that utilize Secure Remote Password (SRP) authentication. |
| -stdname | Displays the ciphers suites in their standard OpenSSL names. |
| -V or --version | This option displays the version information of the ciphers program and exits the command. |
| -convert name | Converts a user-provided ciphers name to its internal OpenSSL format. |
| -h or --help | This option displays a brief help message explaining the syntax and usage of ciphers and then exits. |
| cipherslist | Specifies a list of ciphers suites to be used. Multiple ciphers suites can be separated by commas. |
| @STRENGTH | Sorts the ciphers list based on the encryption algorithm's key length (e.g., @STRENGTH=256 prioritizes suites with 256-bit keys). |
| @SECLEVEL=n | Sets a desired security level (n between 0 and 5) to filter the ciphers list based on its overall security rating. |
| DEFAULT | Shows the default ciphers list configured in OpenSSL. |
Important − The DEFAULT keyword cannot be combined with other options using +. Use the + symbol to combine multiple ciphers suite lists or filtering options.
Examples of ciphers Command in Linux
Here are some examples of the ciphers command in Linux showcasing different functionalities −
Listing All ciphers Suites
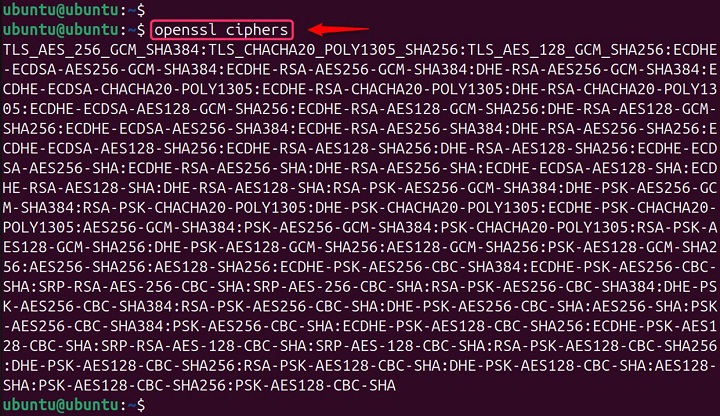
This “openssl ciphers” displays a basic list of all available ciphers suites supported by OpenSSL −
openssl ciphers
Detailed Information with Specific TLS version
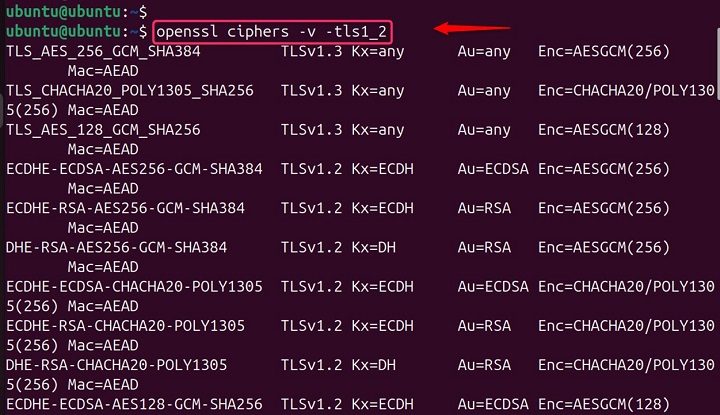
This -tls1_2 shows detailed information about each ciphers suite compatible with TLS 1.2, including key exchange, authentication, encryption, and message authentication algorithms used −
openssl ciphers -v -tls1_2
Filter by Authentication Method
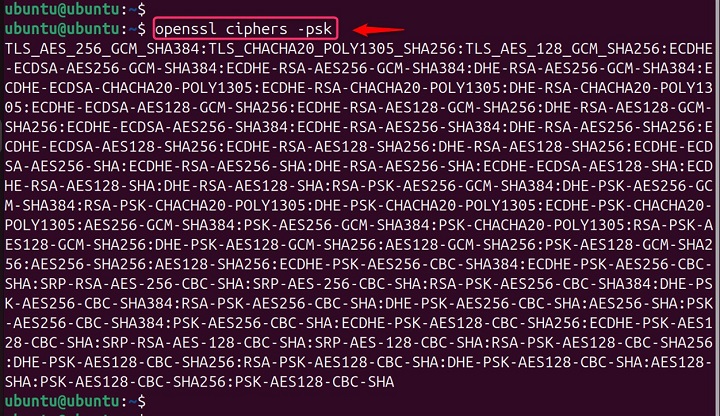
This -psk lists only ciphers suites that utilize Pre-Shared Key (PSK) for authentication, useful for scenarios where a pre-configured key is shared between communicating parties −
openssl ciphers -psk
Prioritize Strong Encryption
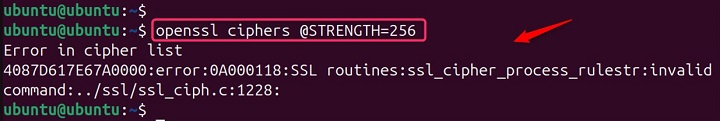
This @STRENGTH=256 prioritizes ciphers suites that use a 256-bit encryption key length, offering stronger protection compared to weaker key sizes −
openssl ciphers @STRENGTH=256
User-defined ciphers List
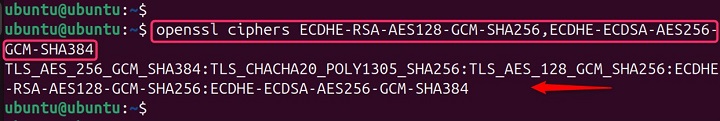
This below command specifies two preferred ciphers suites for a secure connection, forcing the use of these specific options if supported by the server −
openssl ciphers ECDHE-RSA-AES128-GCM-SHA256,ECDHE-ECDSA-AES256-GCM-SHA384
Combining Options with Filtering
This displays detailed information about ciphers suites compatible with TLS 1.2 and filters them to only include those with a security level of 2 or higher (according to some pre-defined criteria within OpenSSL) −
openssl ciphers -tls1_2 -v + @SECLEVEL=2
Check Default ciphers List
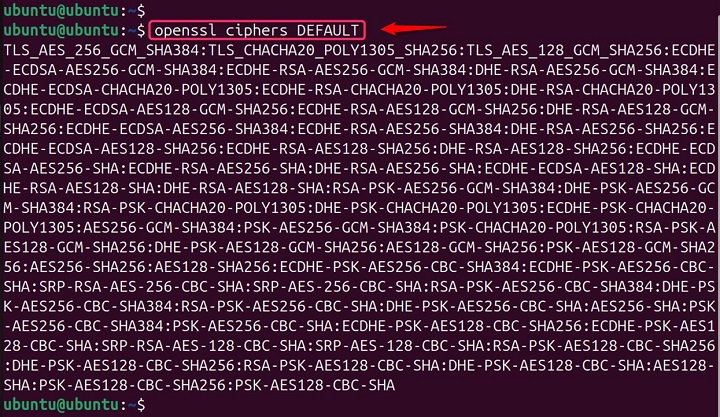
This shows the default ciphers list currently configured in OpenSSL, which might be used by applications that rely on the library for secure communication −
openssl ciphers DEFAULT
Verbose List of All the ciphers Available
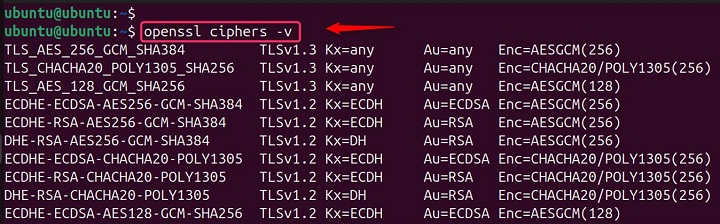
For instance, the command openssl ciphers -v provides a verbose list of all the ciphers available on the system, along with details such as the protocol version, the encryption method, and the key exchange mechanism. This information is crucial for system administrators to ensure that only strong and secure ciphers suites are permitted for use −
openssl ciphers -v
Note − Using the ciphers command effectively often involves understanding the trade-offs between security strength, compatibility, and performance of different ciphers suites. Consulting the OpenSSL documentation for specific ciphers details is recommended.
Remember − Using ciphers effectively requires understanding ciphers suite details and their security implications.
Alternatives of ciphers Command
There isn't a direct alternative to the ciphers command in Linux because it's specific to managing ciphers suites within the OpenSSL library.
However, depending on your specific needs, here are some options that might be helpful −
Disk Encryption Tools
- LUKS (Linux Unified Key Setup) − This is the built-in standard disk encryption solution in Linux. You can manage LUKS encryption with tools like Cryptsetup.
- VeraCrypt − This is a free and open-source disk encryption tool with a user-friendly interface that can encrypt entire disks or individual partitions.
File Encryption Tools
For encrypting individual files, consider these tools −
- gpg (GNU Privacy Guard) − This versatile tool can encrypt and sign files, useful for secure communication and data storage.
- encfs (Encrypted filesystem) − This tool encrypts an entire directory structure, making it transparent to the user.
Secure Communication Tools
- If you're concerned about securing network communication, other approaches exist.
- OpenSSL command-line tools − While not a direct replacement for ciphers, OpenSSL offers various commands like openssl s_client and openssl s_serve
Conclusion
In summary, the ciphers command in Linux is a versatile and powerful tool that plays a critical role in securing communications. It allows system administrators and security professionals to manage and troubleshoot SSL/TLS configurations, ensuring that data remains protected during transmission.
As cybersecurity threats evolve, understanding and utilizing the ciphers command becomes increasingly important for maintaining the integrity and confidentiality of information in the digital age. For those looking to delve deeper into the capabilities of the ciphers command and OpenSSL, there are numerous resources and community forums that offer guidance and support.