
- Unix Commands Reference
- Unix Commands - Home
cryptsetup Command in Linux
The cryptsetup is a command line utility in Linux that lets us encrypt or decrypt a volume. This command is commonly used across Linux distributions to manage disk encryption. It uses the Linux Unified Key Setup (LUKS) standard to create, access, or manage encrypted volumes. However, this command is not pre-installed on most Linux distributions, so you must install it before use.
Table of Contents
Here is a comprehensive guide, we’ll discuss how to install and use the cryptsetup command in Linux.
- How to Install cryptsetup Command?
- Synopsis of cryptsetup Command
- Actions of cryptsetup Command
- Luks Extension of cryptsetup Command
- cryptsetup Command Options
- Man Page of cryptsetup Command
- Usage of cryptsetup Command in Linux
How to Install cryptsetup Command?
By default, the cryptsetup command is not installed on Linux distributions. However, it can be installed using a package manager like apt, dnf, Paceman, etc.
Installing cryptsetup Command in Ubuntu
We can install the cryptsetup command on debian-based systems by running the following command −
sudo apt install cryptsetup
Type y to continue the installation of the cryptsetup command −
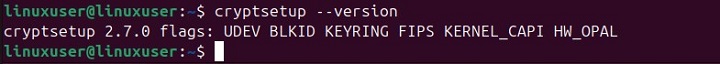
To confirm the cryptsetup installation, type the following command in the terminal and press enter −
cryptsetup --version
The output snippet confirms the successful installation of the cryptsetup command −
Installing cryptsetup Command on Arch Linux
To install this command on Arch Linux, use the Paceman package manager as follows −
sudo pacman -S cryptsetup
Installing cryptsetup Command on CentOS, RHEL, or Fedora
We can install the cryptsetup command on CentOS and RHEL, or Fedora using the dnf package manager, as follows −
sudo dnf install cryptsetup
Synopsis of cryptsetup Command
To use cryptsetup command in Linux, you must follow the below-mentioned syntax −
cryptsetup <options> <action> <action args>
Here, options are the optional flags that can control or modify various aspects of encryption. Action represents the operations that you want to perform while action args provide the necessary details for the action to be performed.
Actions of cryptsetup Command
Here are the valid actions for the cryptsetup command, along with their corresponding arguments −
| Actions | Description |
|---|---|
| create <name> <device> | It creates a mapping with a specified <name> backed by a device <device>, allowing encryption of the device. It supports various options like --hash, --cipher, --verify-passphrase, --key-file, --key-size, --offset, --skip, and --readonly to customize the encryption setup. |
| remove <name> | It removes an existing mapping named <name>. No options are required. |
| status <name> | It reports the status of the mapping named <name>. No options are required. |
| reload <name> | It modifies an active mapping named <name>. It uses the same options as for creation. |
| resize <name> | It resizes an active mapping named <name>. The <options> must include --size. |
Luks Extension of cryptsetup Command
LUKS (Linux Unified Key Setup) is a standard for hard disk encryption. It standardizes the partition header and the bulk data format. LUKS can handle multiple passwords, allowing effective revocation, and uses PBKDF2 to protect against dictionary attacks.
| Options | Description |
|---|---|
| luksFormat <device> [<key file>] | It initializes a LUKS partition and sets the initial key, either by prompting or using a <key file>. Available options include --cipher, --verify-passphrase, and --key-size. |
| luksOpen <device> <name> | It opens the LUKS partition on the specified device <device> and creates a mapping named <name> after successfully verifying the given key material, which can be supplied via a key file with “--key-file” or by prompting. The available options include “--key-file” and “readonly”. |
| luksClose <name> | It is the same as remove. |
| luksAddKey <device> [<new key file>] | It adds a new key file or passphrase to the LUKS setup. We need to provide an existing passphrase or key file using --key-file. The new key file or passphrase is specified as a positional argument following luksAddKey. The available option is --key-file. |
| luksDelKey <key slot number> | It simply removes a key from the key slot. No options are required. |
| luksUUID <device> | It prints the UUID of a LUKS-encrypted device if it has a LUKS header. It requires no additional options. |
| isLuks <device> | It retrieves true if <device> is a LUKS partition; otherwise, it retrieves false. No options are required. |
| luksDump <device> | It dumps the header details of the LUKS partition. No options are required. |
Common Options with cryptsetup Command
The following table illustrates some options accepted by the cryptsetup command −
| Option | Description |
|---|---|
| --hash, -h | It specifies a hash algorithm for password hashing. This option is specifically applicable to “create” action. It supports all hashes accepted by gcrypt. |
| --cipher, -c | It sets a cipher specification string. In older kernels, the cipher specification "aes-cbc-plain" was used while "aes-cbc-essiv" added additional security with ESSIV. Modern systems typically use updated specifications like "aes-xts-plain64" for better protection and support. |
| --verify-passphrase, -y | It prompts for passwords twice, which is beneficial when setting up a mapping for the first time or during the luksFormat process. |
| --key-file, -d | It uses a file for key material. With LUKS, key material provided through -d is used for existing passphrases. To set a new key using a key file, you need to use a positional argument with luksFormat or luksAddKey. |
| --key-size, -s | It specifies the key size in bits, commonly 128, 192, or 256. This option can be used with create or luksFormat, but other LUKS actions will ignore it since the key size is defined by the partition header. |
| --size, -b | It forces the size of the underlying device in sectors |
| --offset, -o | It starts offset in the backend device. |
| --skip, -p | It specifies the sectors of the encrypted data to skip at the start. It changes the IV calculation directly based on the number of skipped sectors, whereas --offset shifts the entire encryption block and adjusts the IV calculation accordingly. |
| --readonly | It set up a read-only mapping. |
| --iter-time, -i | It specifies the number of microseconds to spend on PBKDF2 (Password-Based Key Derivation Function 2) password processing. It is applicable only during LUKS key setting operations, such as luksFormat or luksAddKey, as it controls the time spent on deriving the encryption key from the password. |
| --batch-mode, -q | It doesn’t prompt confirmation. It is only relevant to luksFormat. |
| --timeout, -t | It specifies the number of seconds to wait before timeout. This option is relevant every time a password is requested, such as create, luksOpen, luksFormat, or luksAddKey. |
| --align-payload=value | It aligns the encrypted data payload at a boundary of value 512-byte sectors. It is useful for optimizing performance on RAID setups. By default, it aligns at an 8-sector (4096-byte) boundary. |
| --version | It retrieves the version number of the cryptsetup command. |
Man Page of cryptsetup Command
For detailed understanding, you must access the official man page of the cryptsetup command using the command −
man cryptsetup
The man page includes command’s synopsis, description, basic actions, LUKS extensions, and much more −
Usage of cryptsetup Command in Linux
In this section, we will show you practical usage of the cryptsetup command in Linux −
Initializing a LUKS Partition
To initialize a LUKS partition, run the following command −
cryptsetup luksFormat deviceName
Here, deviceName is the device to be encrypted.
Opening an Encrypted Volume
Run the following command to open a LUKS-encrypted device and map it to a new logical name, making it accessible for use −
cryptsetup luksOpen deviceName encryptedVolume
When you run this command, you will be asked to enter the passphrase for the LUKS-encrypted device.
Closing an Encrypted Volume
Similarly, you can close a LUKS-encrypted volume by using the luksClose, as follows −
cryptsetup luksClose encryptedVolume
This command will unmap the device and close the encrypted volume.
Conclusion
cryptsetup is a widely used command-line utility in Linux for managing disk encryption. It employs the Linux Unified Key Setup (LUKS) standard to secure and handle encrypted volumes. It is not pre-installed on most Linux distributions, however, it can be easily installed using package managers like apt, dnf, or Pacman.
In this tutorial, we covered the installation process for various Linux distributions, explained the synopsis of cryptsetup commands with options, and illustrated practical usage including initializing, opening, and closing encrypted volumes.