
- Unix Commands Reference
- Unix Commands - Home
dgst Command in Linux
The openssl dgst command in Linux generates the "message digest" for a file or standard input. The message digest, also known as a hash, is a numeric representation of data computed by a hash algorithm. It secures the data transferred over an unsafe channel. Moreover, it can also be used to sign and verify digital signatures.
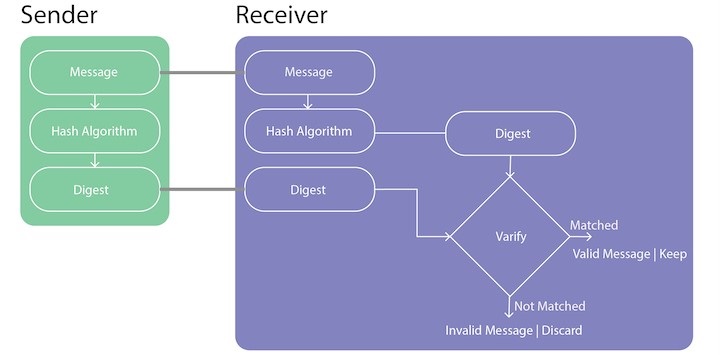
Table of Contents
- Syntax for openssl dgst Command
- Options for openssl dgst Command
- Using openssl dgst Command in Linux
Syntax for openssl dgst Command
The general syntax of using openssl dgst command is as follows −
openssl dgst [options] [file…]
Here, the [options] perform operations like setting the hashing algorithm and signing and verifying the signature. While [file] is the filename whose digest is to be generated.
Options for openssl dgst Command
The options for the openssl dgst command are listed below −
| Options | Description |
|---|---|
| -help | It prints the standard, message digest, and cipher commands |
| -digest | To use a specific digest such as md5, sha512, or shake56 |
| -c | It prints the digest in two digits groups separated by a colon (print output in hex format) |
| -d | It prints BIO debugging details to monitor the I/O operations |
| -list | To print all the message digests |
| -hex | It outputs the digest in hex form (default) |
| -binary | It outputs the digest or signature in binary form |
| -keyform arg | To specify the key format to sign digest (PEM or ENGINE) |
| -out filename | To store the digest in a file |
| -sign filename | To sign the file using the private key |
| -verify filename | To verify the file using the public key (Outputs Verification OK, or Verification Failure) |
| -hmac key | It creates a hashed message authentication code using the mentioned key |
Using openssl dgst Command in Linux
In this section, openssl dgst command usage will be discussed using various examples −
Listing the Supported Digests
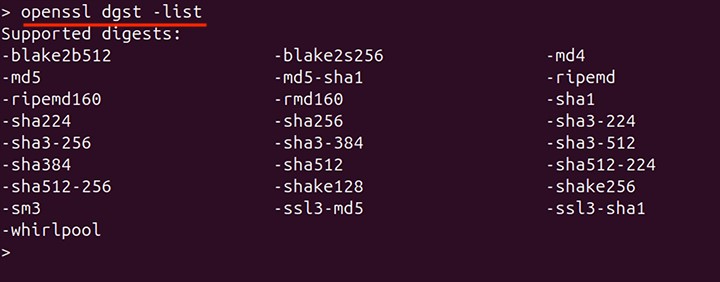
Before creating a message digest, it is important to learn about the supported digests by the openssl dgst command.
To list the supported digests, use −
openssl dgst -list
Generating a Message Digest of a File
To create the message digest or hash of a file, use the command mentioned below −
openssl dgst -md5 file.txt
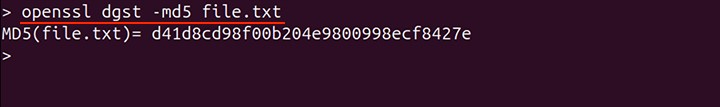
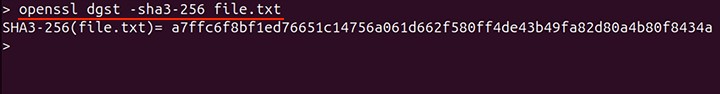
In the above command, the MD5 algorithm is used. To create a SHA-3 message digest replace the -md5 with -sha3-256.
openssl dgst -sha3-256 file.txt
In the same manner, you can generate a message digest using any hash algorithm.
Storing Hash to a File
Instead of displaying the message digest to the standard output, it can also be sent to a file using the -out option.
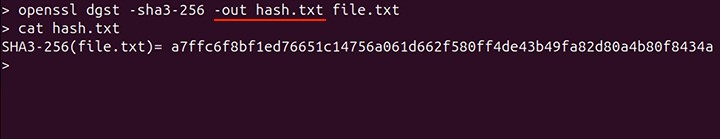
openssl dgst -sha3-256 -out hash.txt file.txt
To view the content of the hash.txt file, use the cat command −
Generating a Message Digest of a File in Binary
By default, the openssl dgst command generates a message digest in hex format. To get it in binary, the -binary option is used.
openssl dgst -sha3-256 -binary -out hash.txt file.txt
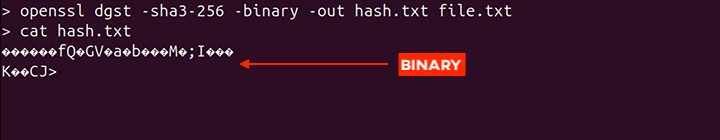
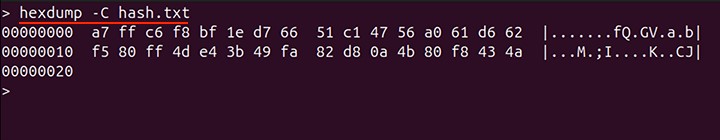
The binary data is not readable because it is not in a human-readable format. To read the binary data on Linux, different tools are used; one of them is hexdump −
hexdump -C hash.txt
Displaying BIO Debugging Information
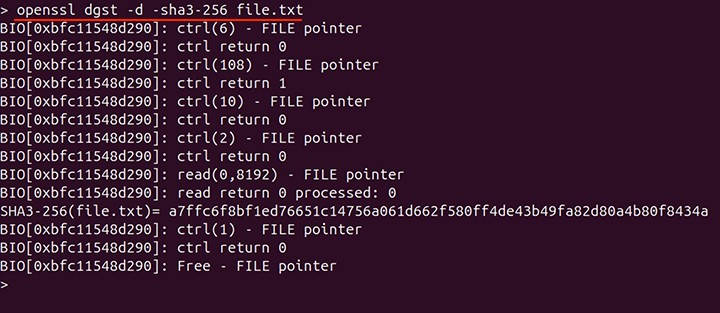
To print the BIO debugging information to the standard output -d option is used. The BIO debugging stands for Basic I/O debugging. This information is used to monitor the BIO object interactions.
openssl dgst -sha3-256 -d file.txt
Signing a File using a Private Key
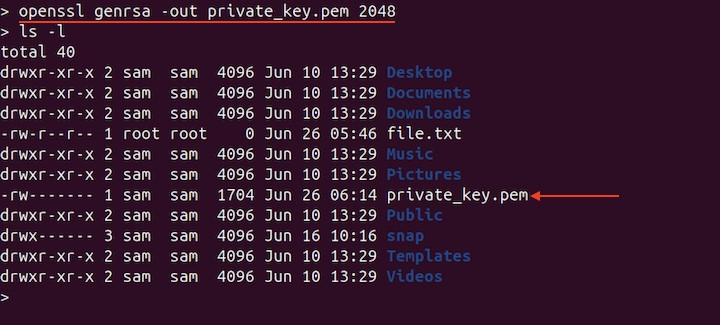
To sign the file using the openssl dgst command, you need to generate a private and public key. To generate a private key, execute the following command −
openssl genrsa -out private_key.pem 2048
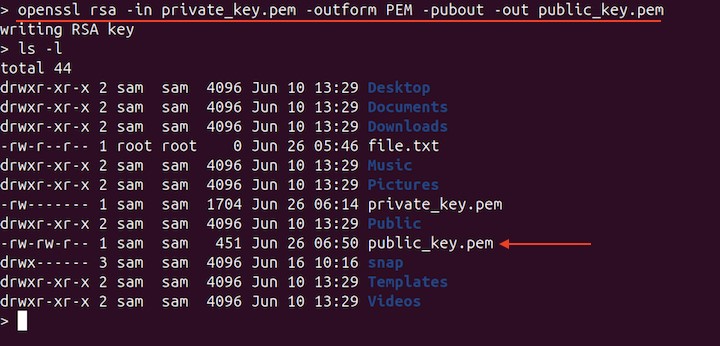
To extract the public key from the private key, use −
openssl rsa -in private_key.pem -outform PEM -pubout -out public_key.pem
To sign the file, use the following command −
openssl dgst -sha3-256 -sign private_key.pem -out signature.sig file.txt
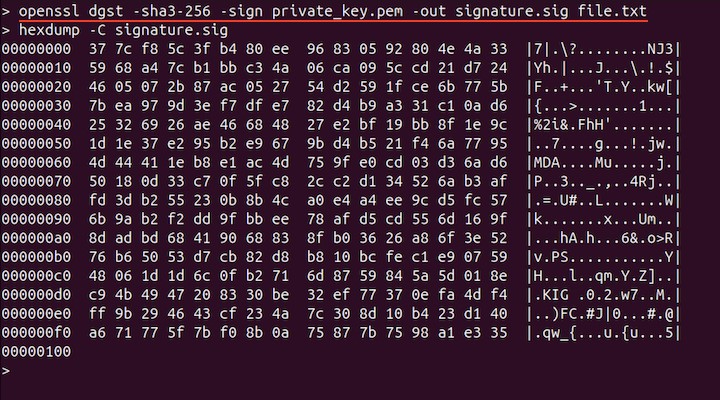
The signature will be generated in binary, to view it use the hexdump command.
Verifying the Signature using the Public Key
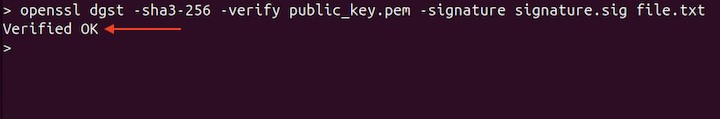
To verify the signature, a public key is needed. The following command verifies the signature.sig against the file.txt file.
openssl dgst -sha3-256 -verify public_key.pem -signature signature.sig file.txt
Generating HMAC of a File
To generate the hashed message authentication code or HMAC, use the private key and file name.
openssl dgst -sha3-256 -hmac "your_key" file.txt
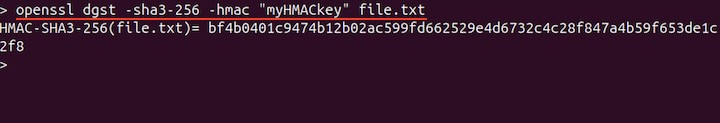
HMAC essentially adds a layer of security to the data in the form of a secret key. To verify the HMAC, run the same command again. If it prints the same output, it means that the data is unaltered.
Conclusion
The openssl dgst command generates a message digest of a file or any input stream. It is used to maintain the integrity of the data while transferring it from one person to another. It supports various hash algorithms; some of them are MD5, SHA3, Shake256, and Whirlpool. Apart from that, it is also used to generate the digital signature and verify it.
This guide covered the openssl dgst command with its syntax and usage using different options.