
- Unix Commands Reference
- Unix Commands - Home
chcon Command in Linux
The chcon command stands for "Change Context" and is used to change the SELinux security context of a file or directory. This is particularly useful when files or directories are moved from one system to another, or when a policy change necessitates a different security context.
The chcon command in Linux allows you to modify the SELinux security context. Context in SELinux defines various aspects of a file's access control, including the user, role, type, and sometimes a range.
Understanding how to use chcon effectively is essential for system administrators who need to maintain the security posture of their systems.
Table of Contents
Here is a comprehensive guide to the options available with the chcon command −
- Understanding chcon Command in Linux
- How to use chcon Command in Linux?
- Examples of chcon Command in Linux
- Alternatives of chcon Command in Linux
Understanding chcon Command in Linux
Before diving into the chcon command, it's important to understand the concept of SELinux. SELinux is a security architecture integrated into the Linux kernel, using a set of rules to enforce the separation of information based on confidentiality and integrity requirements. Security contexts are a part of this architecture; they contain labels that provide a way to match objects (like files and processes) with security policies.
The chcon command in Linux is used to change the security context of a file or directory. This is particularly useful when working with SELinux (Security-Enhanced Linux) where files and directories are labeled with security contexts that define their access controls.
How to use chcon Command in Linux?
To change the full SELinux context of a file, you would use the chcon command followed by the user, role, type, and range in the format of user:role:type:range. To use chcon, you must have a basic understanding of the structure of security contexts, which typically include the user, role, type, and level.
Here's a breakdown of chcon with its various options −
chcon [OPTION]... CONTEXT FILE...
Let’s explain the different options you can use with the chcon command −
| Options | Descriptions |
|---|---|
| -t TYPE | Specifies the new security context type. This is the most commonly used option. The type defines what the file is used for (e.g., httpd_sys_content_t for web server content). |
| -u USER | Specifies the new security context user. This is less common, and modifying the user portion is generally not recommended. |
| -r ROLE | Specifies the new security context role. Similar to -u, modifying the role is not usually necessary. |
| -l RANGE | Specifies the new security context range. This is rarely used and typically managed automatically. |
| -h | Display usage information. |
| -v | Enable verbose output, showing details about each file processed. |
| -R | Recursively change the context of files and directories within the specified directory. This option is useful when modifying the context of an entire directory structure. |
| --dereference | When encountering a symbolic link, affect the file the link points to (the referent) instead of the symbolic link itself. (default) |
| --no-dereference | Opposite of --dereference. When encountering a symbolic link, affect the symbolic link itself, not the file it points to. |
| --reference=RFILE | Use the security context of the reference file (RFILE) to set the context of the target files. This can be a convenient way to apply the same context to multiple files based on an existing reference. |
| --preserve-root | When operating recursively with -R, fail to operate on the root directory (/). This is a safety measure to prevent accidental modifications to core system files. (default) |
| --no-preserve-root | Do not treat the root directory (/) specially. This allows you to (carefully) modify the context of files within the root directory, but use caution as this can have significant security implications. |
| -P | Do not traverse any symbolic links encountered when applying context changes recursively with -R. This can be useful if you only want to modify the context of actual files and directories, not those referenced by symbolic links. |
| -L | Traverse every symbolic link encountered to a directory when applying context changes recursively with -R. |
| -H | If a command line argument is a symbolic link to a directory, traverse that directory (follow the link) when applying context changes recursively with -R. |
| -d | This option removes the category from each specified file or user. |
| -l | With this option, chcat will modify user categories instead of file categories. |
Note − The chcon command allows you to modify the SELinux security context of files and directories, influencing how they are accessed and managed within the system.
Examples of chcon Command in Linux
Here are some practical examples showcasing its usage −
Example 1: Changing the Context of a Single File
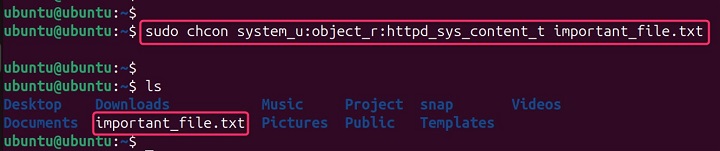
Suppose you have a file named important_file.txt with the default user_u:object_r:user_home_t context (assuming it's in a user's home directory). You want to change its context to system_u:object_r:httpd_sys_content_t so it's accessible by the web server −
sudo chcon system_u:object_r:httpd_sys_content_t important_file.txt
Example 2: Recursively Changing Context in a Directory
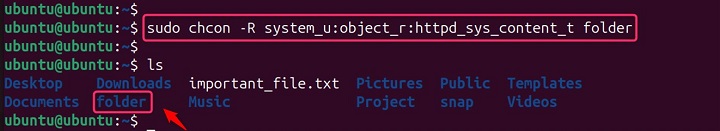
Let's say you have a directory called folder that stores your website content. You want to ensure all files and subdirectories within it have the httpd_sys_content_t context for proper web server access −
sudo chcon -R system_u:object_r:httpd_sys_content_t folder
Example 3: Viewing the Current Context
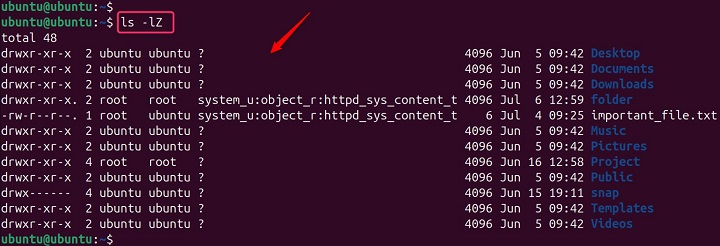
To view the current security context of a file, you can use the -Z option with ls −
ls -lZ
Example 4: Changing the Full Context
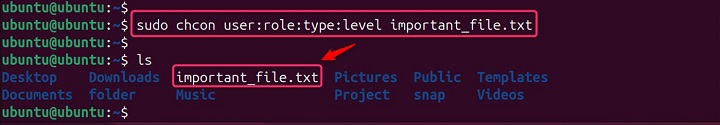
To change the full context of a file, you would use −
sudo chcon user:role:type:level important_file.txt
Note − It's crucial to ensure that the context you're applying is valid within your SELinux policy.
Example 5: Using a Reference File
If you're unsure of the appropriate context, you can use the context of another file as a reference −
chcon --reference=/path/to/reference_file /path/to/target_file
Note − You can also change specific parts of the context, such as the user, role, type, or level, without altering the other parts.
Example 6: Applying Context Based on a Reference File
Imagine you have multiple log files with different names but require the same log_t context. You can use a reference file with the desired context to streamline the process −
touch reference_log_file sudo chcon system_u:object_r:log_t reference_log_file #Create a reference file with the target context (log_t)
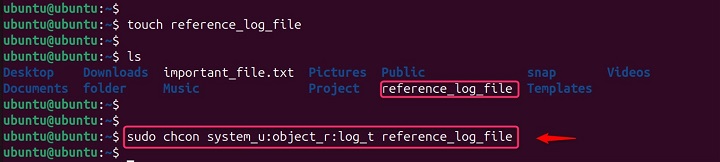
Apply the context from the reference file to all log files in a directory −
sudo chcon --reference=reference_log_file *.log
Example 7: Preserving or Ignoring Symbolic Links
By default, chcon with -R follows symbolic links and modifies the target files. You can control this behavior −
# This modifies the file the symbolic link points to (assuming it's a directory) sudo chcon -R system_u:object_r:httpd_sys_content_t folder # (symbolic link to actual web server directory)
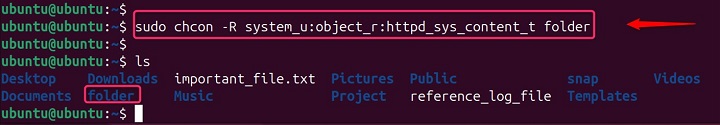
Affecting the Symbolic Link Itself
sudo chcon -R --no-dereference system_u:object_r:httpd_sys_content_t folder (modifies the symbolic link itself)
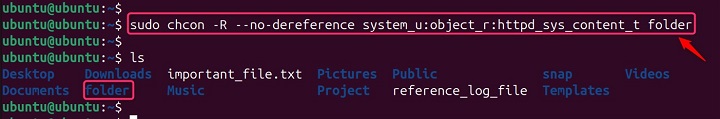
Example 8: Traversing Symbolic Links during Recursion
When using chcon recursively (-R), you can choose how to handle symbolic links encountered within the directory structure −
Traverse All Symbolic Links
sudo chcon -R -L system_u:object_r:httpd_sys_content_t /var/www (follows all symbolic links)
Traverse Only Symbolic Links to Directories
sudo chcon -R -H system_u:object_r:httpd_sys_content_t /var/www (follows symbolic links to directories only)
Skip All Symbolic Links
sudo chcon -R -P system_u:object_r:httpd_sys_content_t /var/www (does not follow any symbolic links)
Refer to your filesystem's documentation for compatibility details. Most chcon operations require root privileges to execute successfully. Use sudo accordingly.
Alternatives of chcon Command in Linux
There isn't a single, direct alternative to chcon for managing SELinux contexts in Linux. However, depending on your specific needs, you might consider these options −
1. semanage fcontext
This command provides a more granular approach to managing file contexts. It allows you to define or modify mappings between file paths and security contexts within the SELinuses policy.
sudo semanage fcontext [-a|-d|-m] CONTEXT matching_pattern[.TYPE]
2. Restoring Default Contexts
The restorecon command can be used to restore default SELinux contexts for files and directories. This can be helpful if you've accidentally modified contexts and want to revert to the system's defaults −
sudo restorecon /path/to/directory
3. Manual Context Editing
For advanced users, context definitions are stored in SELinux policy files. You can edit these files directly (with caution) using a text editor.
Conclusion
The chcon command is a powerful tool for managing SELinux security contexts. With careful use and a good understanding of SELinux policies, chcon can help maintain the security and integrity of your Linux systems. For more detailed examples and advanced usage, consider exploring resources like the SELinux chcon command examples or the Linux Command Library.
Modifying SELinux contexts can have security implications. Use these examples as a guide, but always understand the context types and consequences before making changes. Consult the official SELinux documentation for your specific Linux distribution for further details.